CSRF
CSRF is an attack that tricks the victim into submitting a malicious request. It inherits the identity and privileges of the victim to perform an undesired function on the victim's behalf. For most sites, browser requests automatically include any credentials associated with the site, such as the user's session cookie, IP address, Windows domain credentials, and so forth. Therefore, if the user is currently authenticated to the site, the site will have no way to distinguish between the forged request sent by the victim and a legitimate request sent by the victim.
CSRF attacks target functionality that causes a state change on the server, such as changing the victim's email address or password, or purchasing something. Forcing the victim to retrieve data doesn't benefit an attacker because the attacker doesn't receive the response, the victim does. As such, CSRF attacks target state-changing requests.
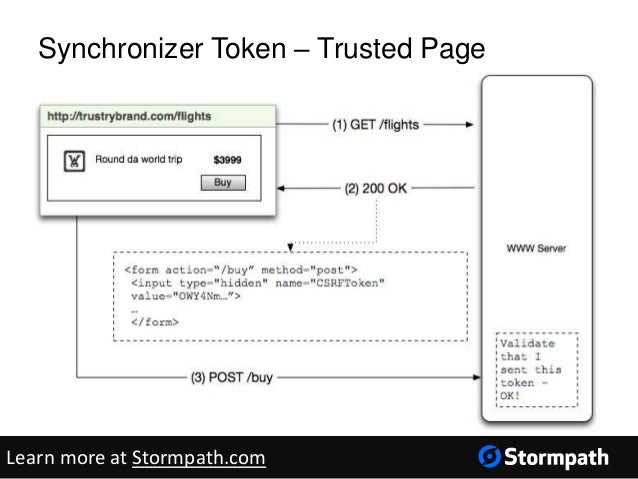
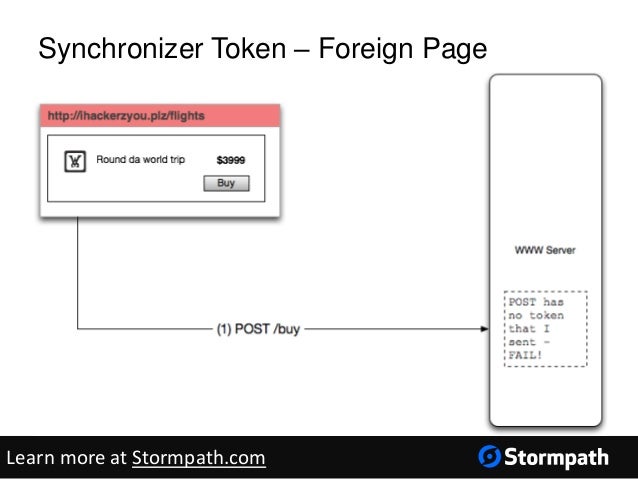
Synchronizer Token as a Protection
Synchronizer tokens are often referred to as “challenge” tokens. These challenge tokens are included within an HTML form and associated with sensitive server-side tasks. When a user wants to execute a sensitive operation the request needs to include the challenge token.
On the server side, the web application verifies that the request includes the token. If it does not, the server rejects the request. Note that this method does require a server side state to be stored and quickly accessible. It is currently considered the best way to prevent CSRF attacks.
Code for the Synchronizer Token Example is found Here
image via : Stormpath.com
image via : Stormpath.com
No comments:
Post a Comment