As I mentioned in the previous post, it is very important to have undetectable payloads if you want to attack a target with anti-malware security controls. Veil 3.0 is another framework which allows us to create undetectable payloads that can be used to attack Windows based targets. Here we are trying to change the signature of known metasploit payloads so we can bypass the signature based detection in anti-virus software. Veil 3.0 is the latest release of the previously known Veil-Evasion framework.
How to install?
First you have to download veil 3.0 from github, You can use git command to clone the veil repository.
git clone https://github.com/Veil-Framework/Veil.git
after the download is finished, move into Veil/setup directory to start the installation
cd Veil/setup
./setup.sh
this will start the installer
this process will take some time and will prompt you to install python and other needed softwares and libraries. Install them if they are not already installed on your system.
Tuesday, October 24, 2017
Sunday, July 30, 2017
Passive Reconnaissance Using Shodan
Shodan is a search engine developed by John Matherly. Even though Shodan is called as a search engine it is different from content search engines like Google. While Search engines like Google crawl through the internet searching for content Shodan scans the internet for open port and grab banners from those open ports. Shodan allows users to search devices connected to internet and obtain information like open ports, services and the service versions of those
Thursday, July 27, 2017
Evading Anti-Virus Detection with Shellter
Anti virus softwares are the last and only defense against malwares in most of the personal computers. So getting through them or evading them is one of the most important thing in penetrating such systems. Payload encoding is one of the method used by attackers to evade detection. You can use metasploit built-in encoders to encode your payloads, but most of the anti virus solutions will detect these payloads. So we need alternatives to evade the detection. Shellter is one of the available solution.
Shellter is able to re-encode windows 32 bit application packages after including the payload or the shell codes so that anti virus softwares will not be able to detect it.
Shellter is not built into Kali Linux, so you have to install it manually. You can either download Shellter from here or use the command apt-get install shellter
Wednesday, July 26, 2017
Linux Basics - Networking Commands
If you are interested in computer security domain, it is important you have a good understanding about networking, particularly networking associated with Linux. so lets take a look at a few basic commands that are used in Linux OS.
ifconfig is one of the mostly used commands when it comes to networking in Linux. It provides you with lot of information regarding the available network interfaces. This command is very similar to the ipconfig command in Windows.
ifconfig is one of the mostly used commands when it comes to networking in Linux. It provides you with lot of information regarding the available network interfaces. This command is very similar to the ipconfig command in Windows.
Linux Basics - File Manipulations
In the previous post we looked into some commands related to file system of Linux. In this post we'll look into some commands related to file manipulation.
As mentioned in the previous post you can create empty files using touch command.
We can use a text editor like vi editor, nano or emacs to edit these files.
vi [filename] will open up the file in vi editor
As mentioned in the previous post you can create empty files using touch command.
We can use a text editor like vi editor, nano or emacs to edit these files.
vi [filename] will open up the file in vi editor
Linux Basics - Directory and File Commands
Before moving to commands related to files and directory manipulation commands, it is important to understand the structure of the file system in Linux.
Unlike in Windows file system where you can find separate partitions like C:/, Linux has a root directory denoted by /. root directory is the beginning of the Linux file system. Root directory contains sub directories and files.
Friday, May 19, 2017
Oauth 2.0 with Facebook
First of all lets see what Oauth 2.0 is, it is an authorization framework that let 3rd party apps to obtain limited and access permission a user account and perform some action on behalf of the user. It uses delegated tokens provided by service that hosts the user account to access user account information. it is important to understand that Oauth 2.0 is not an authentication framework but an authorization framework. Today many sites like Facebook and google provide Oauth 2.0 services.
Friday, April 7, 2017
Encryption
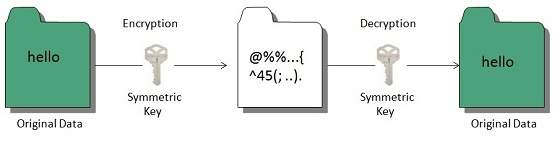
Encryption is a method used to ensure the Integrity and confidentiality of of data. Encryption algorithms convert the data into cipher text which is not readable unless it is decrypted.
Data encryption can be divided into 2 as
In Symmetric encryption a single key is used for both encryption and decryption.
Data encryption can be divided into 2 as
- Symmetric Encryption
- Asymmetric Encryption
Sunday, March 12, 2017
Phishing
Phishing is a type of social engineering attack where an attacker attempts to obtain sensitive information like usernames, passwords or credit card details by pretending to be a trustworthy party to obtain that information. For example an attacker may try to obtain your credentials to your gmail account by sending an email that looks to be from google stating that your credentials need to be verified, and he may include a link to a fake website which looks exactly like gmail login page at the first glance. when you try to login to the site using your credentials attacker will get your credentials and may even display a message stating that you have successfully verified your login details and redirect you to the original gmail login so you can login to gmail.
Subscribe to:
Comments (Atom)