First of all lets see what Oauth 2.0 is, it is an authorization framework that let 3rd party apps to obtain limited and access permission a user account and perform some action on behalf of the user. It uses delegated tokens provided by service that hosts the user account to access user account information. it is important to understand that Oauth 2.0 is not an authentication framework but an authorization framework. Today many sites like Facebook and google provide Oauth 2.0 services.
Friday, May 19, 2017
Friday, April 7, 2017
Encryption
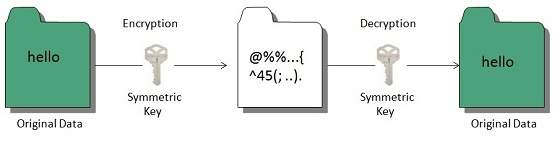
Encryption is a method used to ensure the Integrity and confidentiality of of data. Encryption algorithms convert the data into cipher text which is not readable unless it is decrypted.
Data encryption can be divided into 2 as
In Symmetric encryption a single key is used for both encryption and decryption.
Data encryption can be divided into 2 as
- Symmetric Encryption
- Asymmetric Encryption
Sunday, March 12, 2017
Phishing
Phishing is a type of social engineering attack where an attacker attempts to obtain sensitive information like usernames, passwords or credit card details by pretending to be a trustworthy party to obtain that information. For example an attacker may try to obtain your credentials to your gmail account by sending an email that looks to be from google stating that your credentials need to be verified, and he may include a link to a fake website which looks exactly like gmail login page at the first glance. when you try to login to the site using your credentials attacker will get your credentials and may even display a message stating that you have successfully verified your login details and redirect you to the original gmail login so you can login to gmail.
Subscribe to:
Posts (Atom)